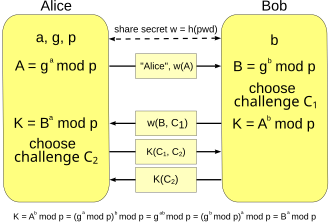
Encrypted Key Exchange (also known as EKE) is a family of password-authenticated key agreement methods described by Steven M. Bellovin and Michael Merritt.[1] Although several of the forms of EKE in this paper were later found to be flawed[clarification needed], the surviving, refined, and enhanced forms of EKE effectively make this the first method to amplify a shared password into a shared key, where the shared key may subsequently be used to provide a zero-knowledge password proof or other functions.
In the most general form of EKE, at least one party encrypts an ephemeral (one-time) public key using a password, and sends it to a second party, who decrypts it and uses it to negotiate a shared key with the first party.
A second paper describes Augmented-EKE,[2] and introduced the concept of augmented password-authenticated key agreement for client/server scenarios. Augmented methods have the added goal of ensuring that password verification data stolen from a server cannot be used by an attacker to masquerade as the client, unless the attacker first determines the password (e.g. by performing a brute force attack on the stolen data).
A version of EKE based on Diffie–Hellman, known as DH-EKE, has survived attack and has led to improved variations, such as the PAK family of methods in IEEE P1363.2.
Since the US patent on EKE expired in late 2011, an EAP authentication method using EKE was published as an IETF RFC.[3] The EAP method uses the Diffie–Hellman variant of EKE.
YouTube Encyclopedic
-
1/3Views:1 905491 874309 510
-
Encrypted Key Exchange - Applied Cryptography
-
Public key cryptography - Diffie-Hellman Key Exchange (full version)
-
Symmetric Key and Public Key Encryption
Transcription
The idea for this protocol comes from Steve Bellovin and Michael Merritt back in 1992. There have been many, many variations on this protocol, many of which are still in use today. This protocol starts from Diffie-Hellman, which you should remember from Unit 3, where each party starts, they have agreed on the generator and some modulus. The client picks a random XA value, raises g to that power, sends the result to the server. The server picks a random XB value, raises g to that power, and sends the result to the client. They can both now compute the same key by raising the value they received to the power of their random value. The problem with Diffie-Hellman for authentication is if there's an active attacker, that attacker can change the values, send something different, set up a shared key independently with each party, and act as a middle attacker intercepting all the traffic because the attacker knows the keys on these 2 separate channels. The idea of encrypted key exchange is to combine this with symmetric encryption to allow the client and server to authenticate each other even if there is a middle attacker. Here's how it works. I assume there's some password that at the beginning of the protocol is known to both the client and the server. Then the way this protocol works, the message that the client will send to the server instead of just being the message that would be sent in Diffie-Hellman is now that message encrypted using the password. So this is symmetric encryption using p, the message that would have been the message in the Diffie-Hellman protocol. And in addition to that, we also need to send the name of the client. So let's say that's Alice. When the server receives this, it can decrypt it and knows this password, and so it obtains the value that would have been sent in the Diffie-Hellman protocol. That means it can compute a key using its secret value XB, combining that with the decrypted result here. As in the Diffie-Hellman protocol, it also sends a message back to the client. In Diffie-Hellman that would just be g to the XB mod q where XB is the secret value selected by the server. Now we're going to combine that with symmetric encryption, encrypting that with the password. Alice decrypts that message, so she can also obtain the value here and obtain the key using the normal Diffie-Hellman technique. So now we'll have a quiz to see if you understand the EKE protocol. The question is, which of these are drawbacks of using the protocol as we've described it here to authenticate a user--that would be Alice on this side-- to a website--that would be the server on this side. The first possibility is that it's vulnerable to offline dictionary attacks. This is where an attacker goes through a dictionary of common passwords trying to guess the password of a user. The second choice is that it requires servers to store the passwords in clear text. And as we discussed in Unit 2, this is never a good idea. The third choice is it's vulnerable to meet in-the-middle attacks just like the Diffie-Hellman protocol was.
Patents
U.S. Patent 5,241,599, owned by Lucent, describes the initial EKE method. It expired in October 2011.
U.S. Patent 5,440,635, owned by Lucent, describes the augmented EKE method. It expired in August 2013.
See also
References
- ^ S. M. Bellovin; M. Merritt (May 1992). "Encrypted Key Exchange: Password-Based Protocols Secure Against Dictionary Attacks" (PDF). Proceedings of the I.E.E.E. Symposium on Research in Security and Privacy, Oakland.
- ^ S. M. Bellovin; M. Merritt (November 1993). "Augmented Encrypted Key Exchange: A Password-Based Protocol Secure Against Dictionary Attacks and Password File Compromise" (PDF). Proceedings of the 1st ACM Conference on Computer and Communications Security. ACM Press. pp. 244–250.
- ^ Y. Sheffer; G. Zorn; H. Tschofenig; S. Fluhrer (February 2011), An EAP Authentication Method Based on the Encrypted Key Exchange (EKE) Protocol.
